Identity-First Security: The Ultimate Shield for a Safer Tomorrow
Whiteswan simplifies cybersecurity by merging identity, network, and compliance into one powerful platform, protecting your critical assets with ease. Transform your security approach with Whiteswan’s comprehensive, identity-centric platform, delivering robust protection and effortless integration across your digital landscape.
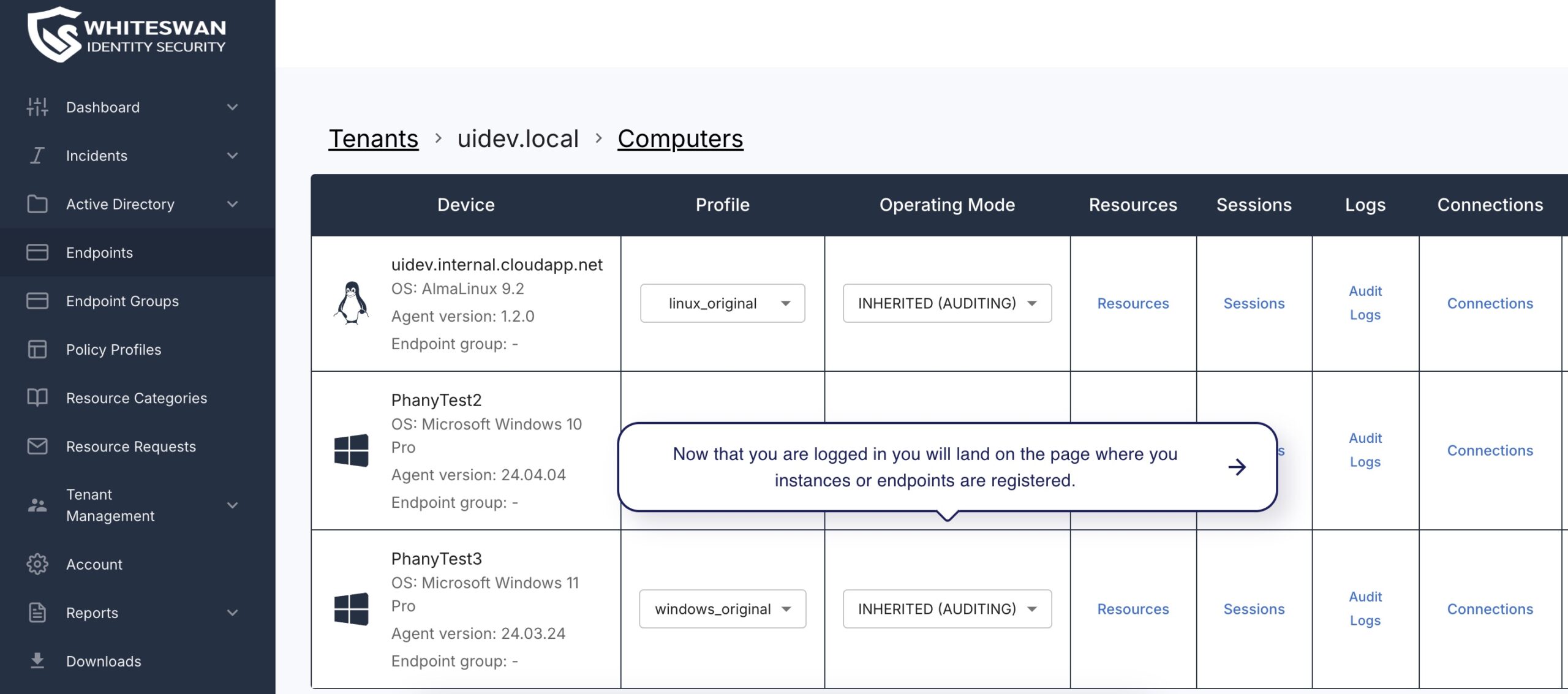
The Power of Identity-First Security
Eliminate permission bottlenecks and human error with automated, time-bound access flows. Ensure complete visibility and compliance through granular permissions and detailed audit logs. Streamline your security operations with Whiteswan’s identity-centric approach, delivering comprehensive protection for your cloud, on-premises, and hybrid environments. Empower your team with swift, secure access to the exact resources they need, exactly when they need them.

Proactive Defense with Identity-First Security
Leverage Whiteswan’s innovative Identity-First approach to establish strong, responsive micro-perimeters around each user and device, enhancing security by preventing unauthorized access and containing potential breaches.

Automated Identity Threat Detection
Utilize advanced analytics to detect and respond to threats in real-time. Whiteswan’s solutions respond instantly to suspicious activities, ensuring that threats are neutralized before they can escalate.
Seamless Integration Across Platforms
Whiteswan’s security solutions integrate seamlessly with existing IT infrastructures, enhancing protection without disrupting user experience or business operations.
Customizable Security Controls
Tailor security settings to meet specific organizational needs with Whiteswan’s flexible security controls. Customize everything from user access levels to security alerts to fit your unique security requirements.
Advanced Features for Complete Security
Whiteswan provides the flexibility and control you need to secure every aspect of your organization, all while reducing complexity and operational overhead.
Granular Access Control
Implement precisely defined access controls that are tailored to user roles and specific job requirements, thereby enhancing security while maintaining operational efficiency.
Isolated Threat Containment
Utilize advanced segmentation techniques to isolate and contain threats within specific network zones, minimizing the potential spread and impact of breaches.
Adaptive Security Policies
Dynamically adjust and enforce security policies based on real-time threat analysis, user behavior, and environmental changes to maintain an optimal security posture.
Streamlined Compliance Processes
Ensure that your security measures not only protect but also comply with industry regulations through automated compliance checks and controls within segmented areas of your network.
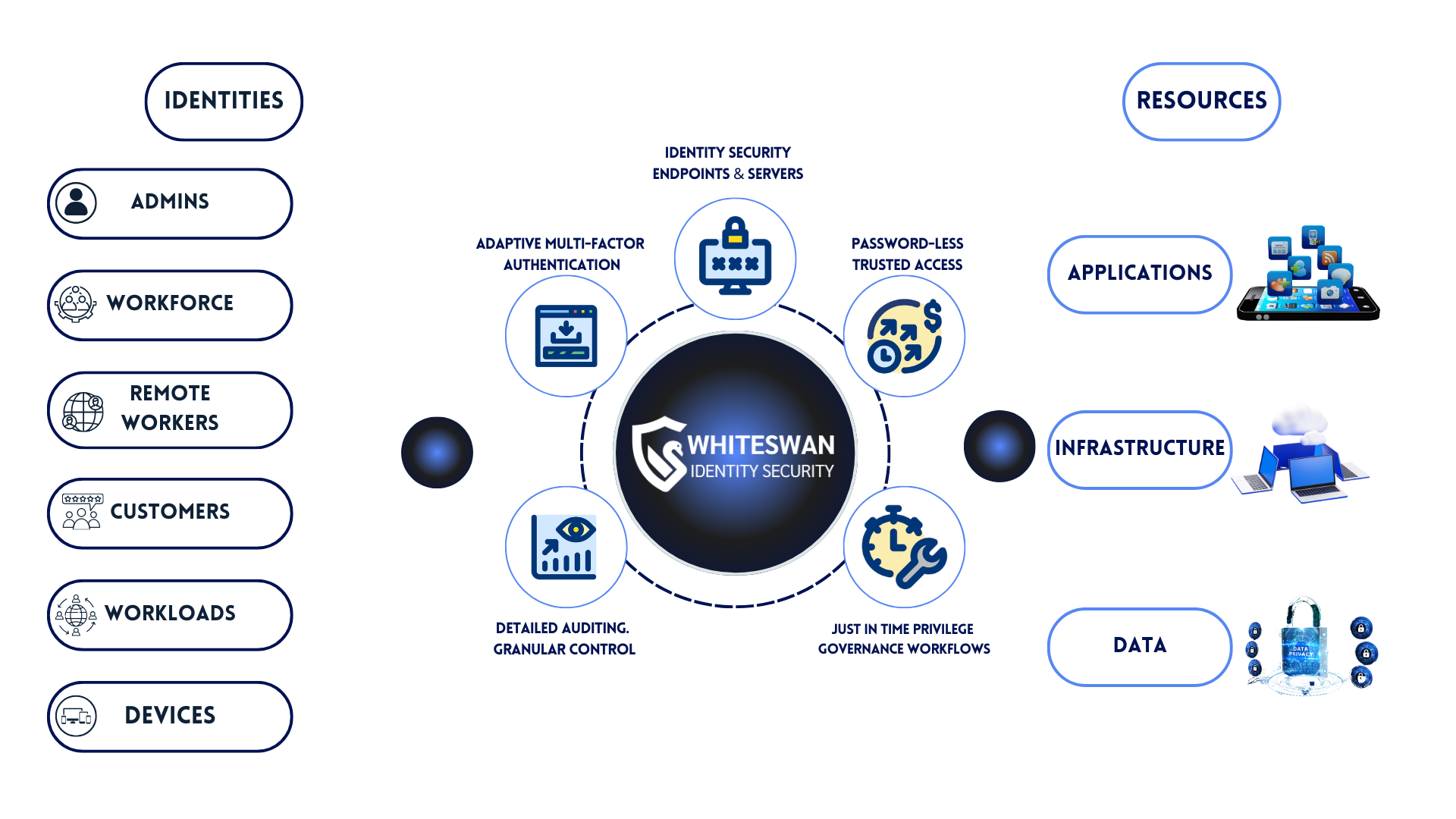
Security That Starts with Identity
Unified Identity and Network Security, Simplified
The Whiteswan Platform consolidates advanced identity, network, and access security into one comprehensive solution. With a focus on Zero Trust principles, our platform continuously verifies each access request, preventing unauthorized access and mitigating the risk of breaches.
- Key Benefits:
- Comprehensive Coverage: Protect users, devices, and networks across on-premises, cloud, and hybrid environments.
- Zero Trust Framework: Continuous verification of every access attempt ensures airtight security.
- Scalable Solution: Adapt and scale your security measures as your organization grows.
Key Capabilities of the Whiteswan Platform
Whiteswan’s platform is built to address the full spectrum of modern security challenges. Each feature is designed to enhance your security posture while simplifying operations.
Key Benefits:
- Zero Trust Remote Access: Securely connect remote users to critical resources without the need for a VPN.
- Identity Segmentation: Apply granular, identity-based access controls to limit lateral movement and enforce least privilege.
- Automated Identity Threat Detection: Leverage real-time analytics to detect and respond to threats before they escalate.
- Seamless Integration: Easily integrate with your existing IT infrastructure for uninterrupted operations and enhanced security.
Why Whiteswan?
Whiteswan’s platform streamlines your security operations, making it easier to manage, scale, and adapt your defenses in today’s dynamic threat landscape.
Key Benefits:
- Simplified Management: Manage all security functions from one platform, eliminating the need for multiple point solutions.
- Zero Trust at the Core: Enforce continuous verification and adapt to evolving security challenges with ease.
- Operational Efficiency: Keep your business running smoothly while maintaining top-tier security across all environments.


Seamless Security, Simplified Management
Whiteswan offers a fully integrated approach to security, combining identity-first principles with real-time threat detection, adaptive access management, and network segmentation.
Key Benefits:
- Unified Platform: Manage identity, access, and network security from one comprehensive solution.
- Scalable Architecture: Adapt to new threats and evolving business needs with ease.
- Automated Processes: Reduce manual effort with automation, improving both security and operational efficiency.
Different Roles Different Needs
Transforming Security Across Roles
Whiteswan offers tailored security solutions for every role, integrating identity and network protection to simplify operations and reduce complexity. Consolidate tools, automate compliance, and streamline access for employees and third parties with seamless Zero Trust deployment, while enforcing MFA and optimizing network performance for complete visibility and security.
Comprehensive Security Management
- Consolidate security tools for both identity and network protection.
- Streamline tactical tasks, focusing on strategic initiatives and enhancing staff efficiency.
- Simplify compliance with automated asset segmentation and centralize access management.
Seamless Integration & Access Control
- Deploy Zero Trust architecture swiftly and simplify network security.
- Streamline employee and third-party access with a single toolset.
- Automatically restrict service accounts, enforce MFA, and manage access efficiently.
Optimized Performance & Network Efficiency
- Segment assets with minimal performance impact and reduce network complexity.
- Utilize software-defined remote connectivity and manage hardware requirements effectively.
- Gain complete insights into account activities and enforce MFA across all accounts.

Whiteswan Identity Security has greatly enhanced our security and streamlined operations. Their precise identity management reduces risks and protects sensitive data. We value their commitment and look forward to ongoing collaboration.

Whiteswan Identity Security has greatly enhanced our security and streamlined operations. Their precise identity management reduces risks and protects sensitive data. We value their commitment and look forward to ongoing collaboration.

Whiteswan Identity Security has greatly enhanced our security and streamlined operations. Their precise identity management reduces risks and protects sensitive data. We value their commitment and look forward to ongoing collaboration.